The FreeBSD Release Engineering Team is pleased to announce the availability
of FreeBSD 9.0-RELEASE. This is the first release from the stable/9 branch,
which improves on stable/8 and adds many new features. Some of the
highlights:
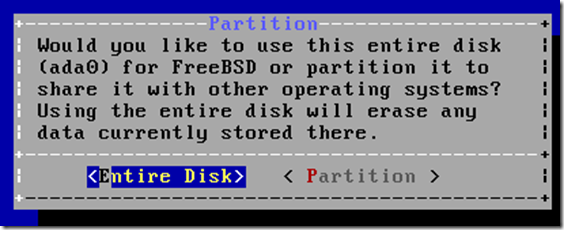
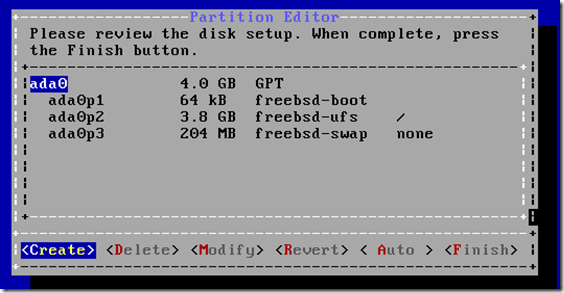
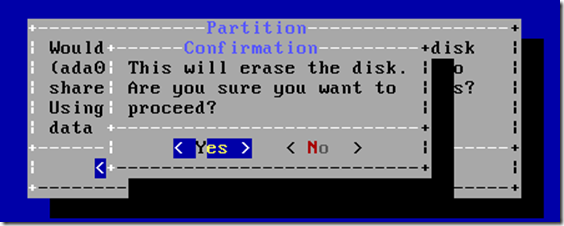
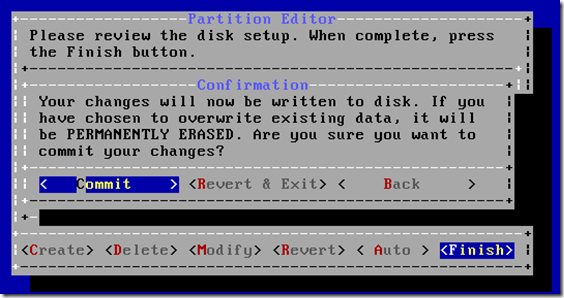
– A new installer, bsdinstall(8) has been added and is the installer
used by the ISO images provided as part of this release
– The Fast Filesystem now supports softupdates journaling
– ZFS updated to version 28
– Updated ATA/SATA drivers support AHCI, moved into updated CAM
framework
– Highly Available Storage (HAST) framework
– Kernel support for Capsicum Capability Mode, an experimental
set of features for sandboxing support
– User-level DTrace
– The TCP/IP stack now supports pluggable congestion control framework
and five congestion control algorithm implementations available
– NFS subsystem updated, new implementation supports NFSv4 in
addition to NFSv3 and NFSv2
– High Performance SSH (HPN-SSH)
– Flattened device tree (FDT), simplifying FreeBSD configuration
for embedded platforms
– The powerpc architecture now supports Sony Playstation 3
– The LLVM compiler infrastructure and clang have been imported
– Gnome version 2.32.1, KDE version 4.7.3
For a complete list of new features and known problems, please see the
online release notes and errata list, available at:
http://www.FreeBSD.org/releases/9.0R/relnotes.html http://www.FreeBSD.org/releases/9.0R/errata.html
For more information about FreeBSD release engineering activities,
please see:
http://www.FreeBSD.org/releng/
Dedication
———-
The FreeBSD Project dedicates the FreeBSD 9.0-RELEASE to the memory of
Dennis M. Ritchie, one of the founding fathers of the UNIX[tm] operating
system. It is on the foundation laid by the work of visionaries like Dennis
that software like the FreeBSD operating system came to be. The fact that
his work of so many years ago continues to influence new design decisions
to this very day speaks for the brilliant engineer that he was.
May he rest in peace.
Availability
————-
FreeBSD 9.0-RELEASE is now available for the amd64, i386, ia64, powerpc,
powerpc64, and sparc64 architectures.
FreeBSD 9.0 can be installed from bootable ISO images or over the
network. Some architectures also support installing from a USB memory
stick. The required files can be downloaded via FTP or BitTorrent as
described in the sections below. While some of the smaller FTP mirrors
may not carry all architectures, they will all generally contain the more
common ones such as amd64 and i386.
NOTE: A problem was discovered with the DVD images for amd64 and i386
architectures shortly after they were loaded on the FTP distribution
server. Those images have since been replaced and we have allowed
enough time that the newer images should have distributed to all the
FTP servers that carry the release. If you downloaded the amd64 or
i386 DVD images prior to this announcement it would be a good idea to
verify the checksums of the image you downloaded with the checksums
provided as part of this Release Announcement. The only thing wrong
with the images that were replaced is that sysinstall(8) can not be used
to install the pre-built packages on the DVD. Other than that there is
nothing different on the updated images. The bad DVD images were never
available on BitTorrent.
MD5 and SHA256 hashes for the release ISO and memory stick images are
included at the bottom of this message.
The purpose of the images provided as part of the release are as follows:
dvd1: This contains everything necessary to install the base FreeBSD
operating system, the documentation, and a small set of pre-built
packages aimed at getting a graphical workstation up and running.
It also supports booting into a "livefs" based rescue mode. This
should be all you need if you can burn and use DVD-sized media.
disc1: This contains the base FreeBSD operating system. It also supports
booting into a "livefs" based rescue mode. There are no pre-built
packages.
bootonly: This supports booting a machine using the CDROM drive but
does not contain the support for installing FreeBSD from the
CD itself. You would need to perform a network based install
(e.g. from an FTP server) after booting from the CD.
memstick: This can be written to an USB memory stick (flash drive) and
used to do an install on machines capable of booting off USB
drives. It also supports booting into a "livefs" based rescue
mode. There are no pre-built packages.
As one example of how to use the memstick image, assuming the USB drive
appears as /dev/da0 on your machine something like this should work:
# dd if=FreeBSD-9.0-RELEASE-amd64-memstick.img of=/dev/da0 bs=10240 conv=sync
Be careful to make sure you get the target (of=) correct.
FreeBSD 9.0-RELEASE can also be purchased on CD-ROM or DVD from several
vendors. One of the vendors that will be offering FreeBSD 9.0-based
products is:
~ FreeBSD Mall, Inc. http://www.freebsdmall.com/
BitTorrent
———-
9.0-RELEASE ISOs are available via BitTorrent. A collection of torrent
files to download the images is available at:
http://torrents.freebsd.org:8080/
FTP
—
At the time of this announcement the following FTP sites have
FreeBSD 9.0-RELEASE available.
ftp://ftp.freebsd.org/pub/FreeBSD/releases/ISO-IMAGES/9.0/
ftp://ftp5.freebsd.org/pub/FreeBSD/releases/ISO-IMAGES/9.0/
ftp://ftp7.freebsd.org/pub/FreeBSD/releases/ISO-IMAGES/9.0/
ftp://ftp8.freebsd.org/pub/FreeBSD/releases/ISO-IMAGES/9.0/
ftp://ftp.au.freebsd.org/pub/FreeBSD/releases/ISO-IMAGES/9.0/
ftp://ftp.cn.freebsd.org/pub/FreeBSD/releases/ISO-IMAGES/9.0/
ftp://ftp.cz.freebsd.org/pub/FreeBSD/releases/ISO-IMAGES/9.0/
ftp://ftp.dk.freebsd.org/pub/FreeBSD/releases/ISO-IMAGES/9.0/
ftp://ftp.fr.freebsd.org/pub/FreeBSD/releases/ISO-IMAGES/9.0/
ftp://ftp.jp.freebsd.org/pub/FreeBSD/releases/ISO-IMAGES/9.0/
ftp://ftp.ru.freebsd.org/pub/FreeBSD/releases/ISO-IMAGES/9.0/
ftp://ftp.tw.freebsd.org/pub/FreeBSD/releases/ISO-IMAGES/9.0/
ftp://ftp.uk.freebsd.org/pub/FreeBSD/releases/ISO-IMAGES/9.0/
ftp://ftp2.us.freebsd.org/pub/FreeBSD/releases/ISO-IMAGES/9.0/
ftp://ftp10.us.freebsd.org/pub/FreeBSD/releases/ISO-IMAGES/9.0/
ftp://ftp.za.freebsd.org/pub/FreeBSD/releases/ISO-IMAGES/9.0/
However before trying these sites please check your regional mirror(s)
first by going to:
ftp://ftp.<yourdomain>.FreeBSD.org/pub/FreeBSD
Any additional mirror sites will be labeled ftp2, ftp3 and so on.
More information about FreeBSD mirror sites can be found at:
http://www.FreeBSD.org/doc/en_US.ISO8859-1/books/handbook/mirrors-ftp.html
For instructions on installing FreeBSD or updating an existing machine to
9.0-RELEASE please see:
http://www.FreeBSD.org/releases/9.0R/installation.html
Support
——-
The FreeBSD Security Team currently plans to support FreeBSD 9.0 until
January 31st, 2013. For more information on the Security Team and their
support of the various FreeBSD branches see:
http://www.freebsd.org/security/
Other Projects Based on FreeBSD
——————————-
There are many "third party" Projects based on FreeBSD. The Projects
range from re-packaging FreeBSD into a more "novice friendly" distribution
to making FreeBSD available on Amazon’s EC2 infrastructure. For more
information about these Third Party Projects see:
http://wiki.freebsd.org/3rdPartyProjects
Acknowledgments
—————
Many companies donated equipment, network access, or man-hours to
support the release engineering activities for FreeBSD 9.0 including
The FreeBSD Foundation, Yahoo!, NetApp, Internet Systems Consortium,
Sentex Communications, New York Internet, Juniper Networks, and
iXsystems.
The release engineering team for 9.0-RELEASE includes:
Ken Smith <kensmith@FreeBSD.org> Release Engineering,
amd64, i386, sparc64 Release Building,
Mirror Site Coordination
Robert Watson <rwatson@FreeBSD.org> Release Engineering, Security
Konstantin Belousov <kib@FreeBSD.org> Release Engineering
Marc Fonvieille <blackend@FreeBSD.org> Release Engineering, Documentation
Josh Paetzel <jpaetzel@FreeBSD.org> Release Engineering
Hiroki Sato <hrs@FreeBSD.org> Release Engineering, Documentation
Bjoern Zeeb <bz@FreeBSD.org> Release Engineering
Marcel Moolenaar <marcel@FreeBSD.org> ia64, powerpc Release Building
Nathan Whitehorn <nwhitehorn@FreeBSD.org> powerpc64 Release Building
Joe Marcus Clarke <marcus@FreeBSD.org> Package Building
Erwin Lansing <erwin@FreeBSD.org> Package Building
Mark Linimon <linimon@FreeBSD.org> Package Building
Pav Lucistnik <pav@FreeBSD.org> Package Building
Ion-Mihai Tetcu <itetcu@FreeBSD.org> Package Building
Martin Wilke <miwi@FreeBSD.org> Package Building, Ports Security
Colin Percival <cperciva@FreeBSD.org> Security Officer
Trademark
———
FreeBSD is a registered trademark of The FreeBSD Foundation.
ISO Image Checksums
——————-
MD5 (FreeBSD-9.0-RELEASE-amd64-bootonly.iso) = 477019a305797186a8b3e4147f44edec
MD5 (FreeBSD-9.0-RELEASE-amd64-disc1.iso) = b23ef73412bd50ed62ef8613ca1a4199
MD5 (FreeBSD-9.0-RELEASE-amd64-dvd1.iso) = 61221643ebeefeeb74bd552311e07070
MD5 (FreeBSD-9.0-RELEASE-amd64-memstick.img) = b37217292ad626d6ab2d3a9c1d215d2d
MD5 (FreeBSD-9.0-RELEASE-i386-bootonly.iso) = 70b4b0dd42c309da79ce63ba2789cfe3
MD5 (FreeBSD-9.0-RELEASE-i386-disc1.iso) = 5bf615f286ee6eeb3ecce45bd8d1622c
MD5 (FreeBSD-9.0-RELEASE-i386-dvd1.iso) = fee32ba2041285b971daf7ea429e36e4
MD5 (FreeBSD-9.0-RELEASE-i386-memstick.img) = 79ddd8f3422e209ae9bd11fee4e399eb
MD5 (FreeBSD-9.0-RELEASE-ia64-bootonly.iso) = 5c83f9a5bf359b2971059d1664ef5f7e
MD5 (FreeBSD-9.0-RELEASE-ia64-memstick) = ee1d5196eb281966b9ef95b953a36d8d
MD5 (FreeBSD-9.0-RELEASE-ia64-release.iso) = 73ca213db21379eb2527dcea37eeb824
MD5 (FreeBSD-9.0-RELEASE-powerpc-bootonly.iso) = bfe036760daac0cddfe8ce2915eaec54
MD5 (FreeBSD-9.0-RELEASE-powerpc-memstick) = e7a09f343ee248ee538954b39549c241
MD5 (FreeBSD-9.0-RELEASE-powerpc-release.iso) = 2431f52b2f9cc1951b0e568b3cd0f126
MD5 (FreeBSD-9.0-RELEASE-powerpc64-bootonly.iso) = 377714742e5f2e16e34b7818347d4e3f
MD5 (FreeBSD-9.0-RELEASE-powerpc64-memstick) = 9e4ee64a7460c3c930d0e3e2e3cd03b9
MD5 (FreeBSD-9.0-RELEASE-powerpc64-release.iso) = 347e51ceb3e65c1eff3cc3acdb519ffb
MD5 (FreeBSD-9.0-RELEASE-sparc64-bootonly.iso) = 81778b8ee1a8881b8597ee4275cc3b4e
MD5 (FreeBSD-9.0-RELEASE-sparc64-disc1.iso) = a63a07e3c45275568db2cead1b3e7167
SHA256 (FreeBSD-9.0-RELEASE-amd64-bootonly.iso) = d16fd5f32c9483177a01241f37ed84f347484c65e52aba4dbf8a2f3108fb457d
SHA256 (FreeBSD-9.0-RELEASE-amd64-disc1.iso) = bcc69320cd2f227411d55967113abc8ffa5ede0a6526090ca3fb5ab776fead9d
SHA256 (FreeBSD-9.0-RELEASE-amd64-dvd1.iso) = f338e24645f0bcc792b8417411ed737d8057cd2f470f9d2b601c143352d6d459
SHA256 (FreeBSD-9.0-RELEASE-amd64-memstick.img) = b8c964f362200d758e06dc6ea8dd556a4d6fedc2f3cd44c300318d9c2f4fb7a5
SHA256 (FreeBSD-9.0-RELEASE-i386-bootonly.iso) = e655de649040269ffdaa40179c3b91c59c8febef7486e340c3a5a5493097366d
SHA256 (FreeBSD-9.0-RELEASE-i386-disc1.iso) = b03df5fbd345781cab7dcab1fd0ea4d84c7c48712a6035476a709e6c0d5763f0
SHA256 (FreeBSD-9.0-RELEASE-i386-dvd1.iso) = ebc75ecdbd0580fbe9e59373962e0fc452c4480082af563e5cd765aca1ecd705
SHA256 (FreeBSD-9.0-RELEASE-i386-memstick.img) = 99193a7895109d415936ba89e4f2c24227af48f064073dee7c4b49722c3656f8
SHA256 (FreeBSD-9.0-RELEASE-ia64-bootonly.iso) = 1d25fc52d868877eb3cbdc012be895827f9c2bd808f886755d7ca2e9257af108
SHA256 (FreeBSD-9.0-RELEASE-ia64-memstick) = af147d20765bdbe6f71a8fb113fdba64de4d152b554c1fc8d78dc6f941e4737c
SHA256 (FreeBSD-9.0-RELEASE-ia64-release.iso) = 289f31e0dadfa46f51e9a44e26cd9cf6652ff4b5a631a21dca065dcd0d66890d
SHA256 (FreeBSD-9.0-RELEASE-powerpc-bootonly.iso) = 7ca03f71d2dd0cad929d0005601b4c994a54b02ab140d4218fa326b0fce7dad8
SHA256 (FreeBSD-9.0-RELEASE-powerpc-memstick) = 042bb4d473b615cf0d3c46d48d4db1fb457a54695e6ef3e47ee1b2dc6a4f3d9b
SHA256 (FreeBSD-9.0-RELEASE-powerpc-release.iso) = 0a7af5c74ebc0e13e79dfde03d54d3d752f3c71aff39659406ad6e5bcc0cefc3
SHA256 (FreeBSD-9.0-RELEASE-powerpc64-bootonly.iso) = 2eb5f141fb702a9c757f91a54ff8ea5ded13d51b29dfa86e5ba6bfbe9bb8e48e
SHA256 (FreeBSD-9.0-RELEASE-powerpc64-memstick) = 91648a0377cd4cf8dc5453e48416dd16ac99a30e5439534053a1ca16f9944a0d
SHA256 (FreeBSD-9.0-RELEASE-powerpc64-release.iso) = 17ab67fe62e1da232038b1ff598be1aef5fe8ccea620e0fbd67d8e262992fd66
SHA256 (FreeBSD-9.0-RELEASE-sparc64-bootonly.iso) = 1f633899cf42be1fecc61f82aa9fd9197da0cf88dda25aabbbf67250653459f5
SHA256 (FreeBSD-9.0-RELEASE-sparc64-disc1.iso) = 8414abb3a501a9f712fe137a2f3667249ab3d2666815a877a93c934ced5d1110
原文链接:http://www.freebsdchina.org/document_28_52946.html